Have you ever struggled to remember a username or password? Join the club.
Wouldn't it be great if you could log in to every site using the same password, without compromising your security? Now you can!
Introducing AgileBits 1Password, the gold standard in decentralized identity & password management for Windows, Mac, iPhone, iPad, Android and unofficially, Linux.
So, what's it do?
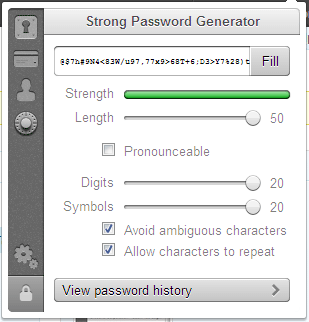
In short, it removes all the hassle from any sign in/sign up process.Next time you're scratching your head trying to think of a sufficiently-secure but memorable password, fire up 1Password. The password generator allows quick and easy access to lengthy, cryptographically strong passwords...
g473/733>{8*:#&T23.F3G]%),2/6.${u9z&7=646L>76XA8,Y
...and I'm supposed to remember that?
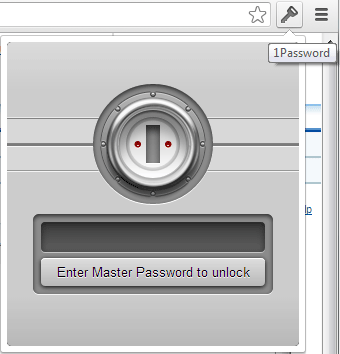
Of course not! 1Password takes care of it for you. Simply sign in to 1Password using a "master" password - which you can choose & change at any time. This is the only password you'll ever need to remember.To sign in, click the 1Password key in your browser. (shown here in Google's Chrome)
After you've signed in to 1Password, simply click the appropriate site from the list to be signed in automatically.
Seems like a lot of hassle... isn't there a shortcut?
Yep. Next time you reach a login screen, just press CTRL + and you'll be logged in automatically.I'm happy with my current passwords, but I hate entering them!
1Password can help there too.Next time you sign in anywhere, you'll see this at the top...
Just hit "Save". Next time, use the shortcut CTRL + and you'll be signed in automatically. You're probably much better off using the password generator though!
But wait, there's more!
1Password also stores credit cards, bank accounts & membership information... it even has a secure notes area; ideal for info which doesn't fall into any other category.What if I forget my master password?
Think... and think hard! You ain't recovering the data any time soon! :)You could try to crack it, but if you're successful, your master password couldn't be all that secure to begin with.
Does it store my passwords securely?
1Password uses sophisticated 128 bit AES encryption (some applications have already been upgraded to AES256) to ensure your identity & password data remains safe.So if AES128 is secure enough, why upgrade to AES256?
I hate the term 'secure', despite my proclivity for using it in various posts here. "Secure" implies there's a point at which it's absolutely safe, which sadly isn't possible.Instead, think of it in terms of its resilience against attack.
In an ideal world, we'd all be using the strongest encryption possible - with limitless iterations through key stretching to further bolster security. Trouble is, from a computational standpoint, encryption (and subsequent decryption) is expensive.
AgileBits' decision to use AES128 was a smart one. It affords immensely strong security to even the slowest of devices without impacting on the usability of either the device, or the software itself. It's sufficient to thwart even the toughest of attacks; taking millions of years to pull off with consumer-grade hardware.
Thanks to the never ending passage of time and Moore's law (no relation ;) ), our equipment is more powerful than ever before... with some smart phones / tablets packing PC-rivaling power and memory.
As such, they're capable of running AES256 just as easily as older devices run AES128.
So to cut to the quick, there's no longer a reason not to use AES256.
Corporate user or paranoid about being watched by NSA / GCHQ?
I am of course, referring to the massively over-hyped PRISM project.Rather than rant on for hours (and honestly, I could!) , I'll give you the short version.
If you've nothing to hide, you're safe. You may not like the thought of being watched, but it has been possible long before PRISM; and will continue to be so long after.
If you've something to hide, you're kidding yourself if you think a $49 application affords you the protection necessary to avoid government involvement in your activities.
But...
Assuming there are no known flaws in 1Password's implementation of AES, HMAC, PBKDF2 or the mechanisms themselves, it will make life very difficult.
Why the emphasis on "decentralized"?
Even the most "secure" encryption can be broken, given enough time and resources. It may take consumer-grade hardware millions of years to break even the simplest of passwords, but who knows what's round the corner. In years to come, super/quantum computers may well be able to reduce that time to a matter of days instead of years... or a weakness may be found in any chosen algorithm. At which point, your only security (rather obscurity in this context) is the hacker needs access to your encrypted files in order to pull off an attack.As 1Password is entirely decentralized, there's no requirement to share your encrypted data with anyone... it will work quite happily on just your PC.
The competition...
Let's take a brief look at 1Password's competition.KeePass (keepass.info)
I like to spend at least a couple of weeks with a product before reviewing/purchasing it... but the decision to avoid KeePass was made in less than a minute. Why?
-
The installer is sent over HTTP - which cannot be trusted. How do I know I'm downloading the real "KeePass" application and not an insecure & malware-ridden fake?
-
The "integrity" hash sums, PGP signatures and .NET public keys are also sent over HTTP - which cannot be trusted. What's the point of releasing hashes to confirm the integrity of a download, when the hashes themselves are sent over an insecure protocol? Crazy!
RoboForm (roboform.com)
Although the RoboForm installer is sent over HTTP, it's digitally signed meaning we can check it hasn't been altered before installation.
However, anyone actively using the term "military grade encryption" really should be shot at dawn. Their use of PBKDF2 which, to the best of my knowledge is just 1000 iterations, is simply not enough either.
LastPass (lastpass.com)
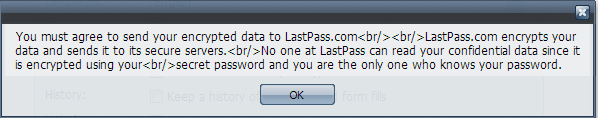
LastPass is interesting. It uses similar encryption to 1Password (fewer iterations through PBKDF2 though - at just 5000, so quicker but less secure) with one main difference... your data is stored online.
Ignoring the botched carriage returns for the moment, it essentially means you can't use LastPass without storing your data at LastPass.com.
That worries me. Sure, it's encrypted using your "secret password" and it's probably "safe" - but it's unquestionably safer to keep your encrypted data off the internet in the first place.
What happens if LastPass.com are hacked?
The official line is as follows...No one at LastPass can ever access your sensitive data... our best line of defense is simply not having access to data even if someone got in. If LastPass can't access it, hackers can't either.My viewpoint is somewhat different.
The hacker might not be able to immediately view your passwords without breaking the encryption first, but they could insert malicious javascript to intercept your "secret password", and that would take just a few seconds. To say nobody could ever access your data is incredibly naive and misleading. One disgruntled employee, one server breach and bang... it's all over.
Use multiple devices?
Although 1Password is decentralized, it also has native support for Dropbox; allowing your data to be seamlessly synchronized across your devices. Not a fan of Dropbox? Drop your 1Password files on Google Drive or even on a USB stick... you'll be able to access your details anywhere using the contained HTML file. You'll need a modern browser however... IE users are out of luck I'm afraid.You said avoid storing encrypted data online - you've changed your tune!
It's important to weigh up the potential risk with the added benefits of synchronizing via the web.The encrypted data, on its own, is of little use to anyone. A password, on its own, is of little use to anyone.
The reason LastPass concerns me is because they handle both your data and the authentication process in one place. With 1Password, the authentication process is handled offline... so theoretically, your data can be stored anywhere with minimal risk.
Security: You need a strong foundation.
The ironic and nonsensical nature of delivering unsigned security products over HTTP never ceases to amaze me. HTTP data cannot be trusted, under any circumstances. Those hash/PGP keys are worthless too, for much the same reason.KeePass/Roboform might be secure. They might be bulletproof... but unless you can be sure it's the genuine article, everything else pales into insignificance.
AgileBits know this, hence why they deliver both the product and subsequent updates over HTTPS.
But AgileBits aren't without flaws...
SSL
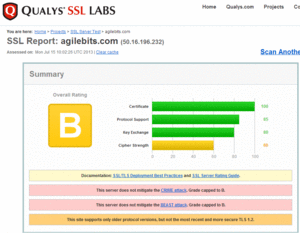
No PCI compliance (despite accepting credit card payments directly) and vulnerable to both BEAST and CRIME attacks. Hmm...
I contacted Jeff Goldberg at AgileBits to find out what's going on.
We’ve been aware for some time of the somewhat embarrassing fact that our secure web server hasn’t been up to standards in the algorithms it offers for encryption. We have ensured that our site certificate uses the hight standards for authentications; so people visiting the site and downloading from it can be confident that they are getting things from us and not an impostor. This is where our site security matters the most, and in that we provide excellent web site security.It would be difficult for a hacker to position him/herself correctly in the network such that a BEAST attack would be possible. It's a risk, but a minimal one in my opinion. Allowing compression however (thus CRIME) is just plain lazy... but at least Jeff agrees.
With respect to CRIME, I’ve got no excuses. We should be able to disable compression with no adverse consequences.
Jeff is actively working to resolve the SSL issues.
KeyChain Tampering
Here's a little known exploit - but one which deserves more air time. 1Password uses a KeyChain to store your usernames/passwords. The contents of each field are obviously encrypted, but the locations at which they're used are not.For example... here's my LastPass test data in 1Password. I've added carriage returns to make it easier to read.
{
"keyID":"C5459C772DD7484CA5BEDF289B3961A0"
"locationKey":"lastpass.com"
"encrypted":"U2FsdGVkX1/U0VB8/D2xFYME7IVN25XMzt5+7rNjEf/ciZ6g/NfkvKUmbhXhNKiLakAnywSJ1LRxiusQPi6DmRsVTk1d7tlvJhcvYUxsP5uZueQYXlsjcuNZ3yIdKlPTLBTnrDDfwFxZ2cxMpZHYMuh0fav5R0f/al3d6y9/lTl2atjIE7Ddjfi+cNl4mCwDIi7r1q/jsr201e98hxpKmzmGUyT8bIAQqbV44le/sfufgs9HK4lUBALkXWfTM3WabGy03iqNpYBevg1y+j1G2L4kgWfmLYp2JIDu/njLoRD0AVp3elfOUZJU3subydmTy3x8ZA0bd4N+xfa6RdmSPes+hmLOjW2Xriyhyq9AkRTjrZ+nuvyHU7xKMRjiJl2HijBtbEPHNZSBzGS3ri3u4B3BssqMLds5rrnUKdA032aIlHfXCAQTBBl46Q9s4KXbTqXyOHWeFyAQkogLz+HvEnbSrUaUNgidQqbql4ma2zZM5iZ805/HTRfrxKjdXRWU5eQrLYwbXgKR0qDE6uXukBQzRdFFtIHMTrNb4uoXcgI9dJMMBMPibhz99uFGX075Hn7IWis198=u0000"
"typeName":"webforms.WebForm"
"location":"https://lastpass.com/index.php?&ac=1&fromwebsite=1&newvault=1&nk=1"
"uuid":"E095FE4CF398373353407A0DC9296ACF"
"updatedAt":1373915388
"createdAt":1373892417
"title":"lastpass-fake.com"
,"contentsHash":"242900b6"
,"securityLevel":"SL5"
,"openContents":{"autosubmit":"default","usernameHash":"bd8f9f171e9d74041b69299aeef59f05c93d31a5d885b322227e02c458a5ef82","scope":"Regular"}
}
Have you spotted the obvious design flaw? You're able to change the "location" parameter without knowing the encryption key. Furthermore, there's no MAC authentication on the field... so 1Password diligently imports the data with no obvious difference for the user. All you have to do is wait...
... and wait ...
... and next time the user clicks that record (which still appears as "lastpass.com" (see title param), it loads a fake site and passes both your username & password in plain text. EEK! I'll email Jeff again to get his comments... and update the article if necessary.
Mitigating other risks...
You wouldn't dream of giving your bank account details/PIN number to a complete stranger, and yet we're expected to share our personal information online with absolutely no guarantee that it'll be safe. Privacy policies (regardless of eloquence) can only go so far - and they're usually written by legal teams with absolutely no understanding of how the technical architecture works. For many firms, it's more a box-ticking exercise than something they truly abide by.Unfortunately, cases of poor password management are commonplace... with many companies still storing them in plain text. Take Companies House for example - potentially storing in excess of 30 million passwords in plain text. Incredible.