Update(s):
18/Dec/2012 - One SSL bug now fixed (might want to put security testing out to tender next time!) - but still a few to go. Directory traversal still possible... hint encode/escape or strip, don't add slashes! Significant improvements have been made to the SSL implementation - now scoring a healthy Grade A @ Qualys SSL Labs. At least progress is being made... can't fault them for that.
17/Dec/2012 - WebCheck now uses cookies - but still not secure! At this point, I'm not sure what's worse... the existence of the flaws or their proclivity for botched updates. Perhaps a report to the ICO would help... or not.
13/Dec/2012 - Unfortunately, there has been no further correspondence since my email dated 5/Dec/2012.
Since then however, several new issues have come to light... including 1 directory traversal exploit which could reveal the codebase of both WebFiling & WebCheck. SSL encryption is still not enforced on vital pages of WebFiling - allowing any account to be hijacked. There's still no word on password/token hashing either - there's no justifiable reason why this can't be released. If it's securely hashed, so much the better. If not, why not?
The latest directory traversal exploit coupled with an outdated & vulnerable perl installation (5.8.5 - from 2004!) means that once again, the system is insecure and users are being put at risk. This time however, the exact details will remain private & confidential until they are identified & addressed by developers/penetration testers. A disclosure of any sort (partial or otherwise) at this time could directly place the system and every user at immediate risk.
I am currently working with another security consultant to record a simulcast which demonstrates exactly how anyone can hijack a company. It's live, detailed and absolutely unequivocal proof that it's possible... even as of 13/Dec/2012. Look out for that!
10/Dec/2012 - Companies House have now rectified the flaws which allowed session hijacking in WebFiling. (see above) WebCheck is still vulnerable, and it still isn't clear how the passwords are stored. Until such time, we must assume they are still stored in plain text and as such, you should you exercise caution when choosing your password; it may be visible to database administrators and other members of staff.
14/Nov/2012 - Part 2 is now live: http://ramblingrant.co.uk/2012/11/14/companies-house-security-review-part-2/
More updates as/when they're available.
"YOU’LL ONLY LOSE YOUR COMPANY ONCEBetween 50-100 cases of Corporate Identity Fraud occur every month."
Source: http://www.companieshouse.gov.uk/infoAndGuide/coIdFraud.shtml
Preface
If you own/run a company in the UK, this directly affects you.This article outlines a catalogue of very serious security flaws at Companies House; any one of which could place your company at significant risk of identity theft.
The following is a result of a seemingly innocuous request to reset a password. Unfortunately, it has led to an almost unbelievable display of ignorance & incompetence. Please take the time to read & digest it. If technical details bore you and you'd rather cut to the chase, skip to the summary.
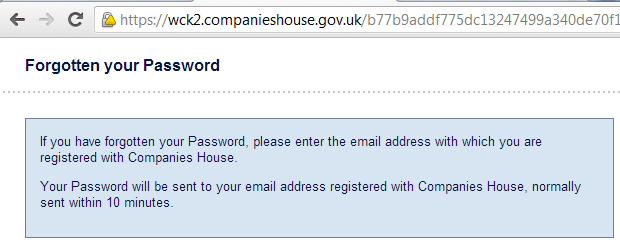
On October 1st 2012, I needed to reset my WebCheck password at Companies House.
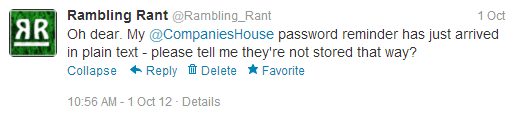
Sure enough, I later received an email with the password in plain text. Amazed, I decided to tweet Companies House (@CompaniesHouse) to check if this was normal...
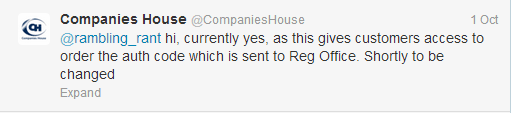
The response was shocking...
For a system which is purportedly "much safer and more secure than paper submissions", that isn't a great start. It does mention that it's due to change soon... but it does beg the question - Why was it designed that way to begin with?
As a security researcher & consultant, this really is the metaphorical "red rag to a bull", so I decided to delve a little deeper and see just how safe it really was.
I called Companies House and asked to speak to the technical team or indeed anyone responsible for security within the authority. The customer services rep asked what the call was regarding, so I explained the situation in the simplest terms possible and waited to be put through.
"Those are sent automatically by a machine, so nobody can see it"Phew! For a moment there, I thought it wasn't safe. When I explained why that wasn't relevant, I was put through to the WebFiling department and had to explain the problem again.
"That's not my department, I'll put you through to WebCheck..."After a couple of pointless trips around customer service reps, I'm eventually answered by Tanya and yet again, had to explain the problem. I asked again to speak with a Technical Consultant... only to be told they're "the untouchables" and aren't reachable by phone. Instead, I could leave my name and number with her and she'd get back to me.
True to her word, she called the following day to say she hadn't forgotten, but hadn't heard back as yet. Later, she called again... this time with a response not from the technical team, but the Press department!
"Companies House takes information security extremely seriously. [snip] We already have a range of security controls in place to protect information. We are certified to ISO27001 standard and adhere to the government's Security Policy Framework. [snip] Our systems and services are regularly penetration tested to further validate the controls we have in place."That's not really what I was after... especially as it appeared to be complete nonsense.
Undeterred by their response, I carried out some very basic tests which any secure, penetration-tested site should easily brush off. When I say basic, I mean basic... think script kiddie level and you wouldn't be far wrong.
Passwords
As any security-conscious person will tell you, passwords should never, under any circumstances be visible in plain text. Storing and disseminating them in this manner is absolutely ludicrous and a major security risk.To make matters worse, you're forced to choose a weak(er) password to begin with.
"The password must consist of between 4 and 8 alpha-numeric characters"You're not allowed to use special characters either, but dictionary-based words are fine... you can even use your name!
SSL
This is a difficult topic and well beyond the scope of this article. Suffice to say, the site is more than willing to pass private, confidential information over the wire without any form of encryption. Sure, they have an SSL certificate but in reality, the way it's implemented renders it almost entirely useless.Server Applications
404 Not Found, 403 Forbidden, 500 Internal Server Error... we've all had an error message at some point, but they frequently include information which you really shouldn't see.The errors shown by Companies House for example, also include what version of software the server is running. Apache 2.0.52 in this case... released a whopping 8 years ago. Now... it is possible to alter (fake) that information for reasons I won't detail now, but assuming that's correct... the security problems go deeper than first thought.
XSS (Cross Site Scripting)
Cross Site Scripting exploits the trust a user has in a web page. If you load a page from http://www.companieshouse.gov.uk, you'd expect that every piece of information you see has been put there by Companies House. That's usually the case, until an XSS flaw is introduced. XSS allows a hacker to alter what you see, how the page functions and take control of the entire page.XSS can be broken down in to different types, including but not limited to "reflected" and "stored". Reflected attacks are the most common and requires you to use a link which contains a malicious payload... usually by email, web post or tweet. Once clicked, the payload takes effect and the damage has been done.
Stored attacks are far less common, but just as dangerous and easier to implement for the hacker. With a stored attack, the hacker usually doesn't need your input... the malicious payload is stored by the server and if you're unlucky enough to visit an infected page, the payload takes effect and again, the damage is done.
Sadly, Companies House are vulnerable to both. It's not just one vulnerable page either, virtually every page is wide open to these attacks. An SSL certificate (even when implemented properly) provides no protection against this type of attack.
XSRF/CSRF (Cross Site Request Forgery)
Cross Site Request Forgery exploits the trust a web site has in a user (note it's reversed from XSS). If a site is vulnerable to this type of exploit, it's possible to trick it in to believing you've carried out an action yourself. For example, say you want to change your password. With CSRF, a hacker can do that for you... and worse, the site is none-the-wiser as it's actually your machine that carries out the request. Note, they don't have access to your machine as such... just your session with Companies House.Cookies & Session Information
Cookies, when used correctly, are generally accepted to the safest, most secure method of storing information in the browser. For many sites, cookies play a crucial part in improving user experience, monitoring activity and managing session information.The other option is known as a "cookie-less session"; it's far less secure, introduces many drawbacks and as a result, they're not widely used.
Guess which Companies House use? You guessed it...
What are the risks involved with cookie-less sessions?
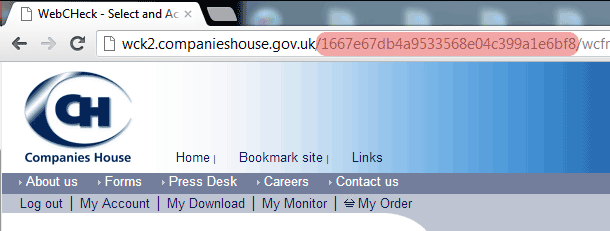
If someone obtains your session ID (a unique reference assigned to you when you login), they can access your account without knowing your username or password.The value shown in red is the session ID. The "My Account" option allows you to view your profile (name, address, phone number, email address) & order history (companies you monitor, forms you've ordered).
Wait... there's no SSL!
If you spotted that, consider your back well and truly patted.Without SSL, that "secure" session ID has been sent over the wire without any form of encryption, so anyone can read it. If you use a shared network, open WiFi, off-shore/outsourced IT or an ISP... can you trust everyone in the loop to look after that vital piece of information? This kind of attack is known as MITM or Man In The Middle, in that the data can be intercepted/altered before it reaches you.
Does it happen... yes, and it's getting more prevalent. Sophisticated attacks like this are rarely detected until it's too late. Remember, you'll only lose your company once.
If it's a sophisticated attack, surely the chances of this happening to me are low?
Unfortunately not. An MITM attack is just one way to obtain the session ID, here are some others.- You copy/paste a link to a friend, not knowing it contains information which puts you at risk.
- You run browser add-ons which monitor the contents of the address bar - think Rapport, anti-virus/malware applications.
- Your machine is infected with malware or a virus.
- You click an external link on Companies House.
That last one might confuse you. You may have noticed these at the bottom right of each page...
Have can leaving a vulnerable site increase the risk?
Sounds daft, but bear with me.When you visit a site, your browser shares various pieces of information... including your operating system & browser version. When you click a link on a site, it passes a value known as the referer. This tells the destination site where you came from.
With a traditional cookie, there's no immediate risk. With a cookie-less session however, there's one obvious problem... the address we came from contains your session ID (in red above).
By leaving the Companies House site via those links, you've inadvertently given out the single most important piece of information that keeps you safe. Now you must trust everyone involved in that organisation too and assume their own systems aren't vulnerable.
Shocked yet? Let's keep going...
If someone steals my session ID - wouldn't Companies House notice it's not my PC?
If Companies House were secure, you'd be correct. Unfortunately, there are absolutely no safeguards in place for this either.Try it yourself.
Open your favourite browser and login to Companies House.
Copy the entire contents of the address bar.
Open a different browser and paste the contents... you're now logged in. No usernames or passwords required.
The same applies for different PC's, internet connections and even countries. To test this theory, I connected to a remote server in Germany and pasted the same link - it let me straight in.
If you're really observant, you'll note I've only shown WebCheck so far as opposed to WebFiling (needed to steal a company's identity).
Is WebFiling also vulnerable?
Of course, did you expect anything less at this point?With a few minutes work, I've absolutely no doubt the above information could be used to hijack a company. Given a few hours/days of planning, it may be possible to steal a company's identity in such a way that Companies House would struggle to locate any instance of fraud.
Summary
The Companies House site is absolutely festooned with very serious flaws and doesn't appear to have been penetration tested recently, if at all.At the present time, I'd argue that submitting returns in paper form is actually safer but please keep in mind, if you're registered for PROOF ("Protected" Online Filing), you can't submit in paper form without a letter from the Directors.
I've had a response from Companies House addressing many of these issues, but for legal reasons I cannot discuss the contents at this time.
There's more to come, so stay tuned.
Companies House Official Response #1 (09/10/2012)
"Thank you for contacting us about this important matter. Companies House takes information security extremely seriously - as well as any concerns raised by customers or the public. We make every effort to review these to make sure we continue to provide the best security available and to meet our customer's expectations. Such issues are especially welcome if specific issues are raised. As a result we are able, as in this case, to verify the matters raised and confirm that security arrangements were already fully in place or that issues were already identified and being addressed. Our systems and services are regularly 'penetration tested' to further validate the controls we have in place.We already have a range of security controls in place to protect information. We are, for example, certified to the ISO 27001 standard and adhere to the government's Security Policy Framework, which offers further reassurances to our customers regarding our standards. Potential security risks are continually assessed to ensure we have controls in place that provide an acceptable level of mitigation, which keeps these to a minimum."
Comments to reply #1
If you're thinking "that looks familiar"... it's an almost identical response to the one I had before raising these issues. If this is an example of a site which adheres to the government's Security Policy Framework, is ISO27001 certified and has been penetration tested - should we trust any government department with our information?I would like to take the opportunity to thank Troy Hunt (@troyhunt) and everyone else that has tweeted this article. Your efforts have raised awareness with literally tens of thousands of businesses & individuals, many of which have already been in touch for info on how to protect themselves. (more on that later). Spread the word.