Be Cyber Streetwise is a cross-government campaign, funded by the National Cyber Security Programme, and delivered in partnership with the private and voluntary sectors. The campaign is led by the Home Office, working closely with the Department for Business, Innovation and Skills and the Cabinet Office.
On January 13th 2014, I read an article on the BBC website about a new government initiative on cyber security called cyberstreetwise.com.
With the above description in mind, I had a quick look through the site with a view to promote it through various channels we use at work. What a great idea! A collaborative effort by government and industry professionals working towards a common goal; promoting good security practice to consumers & SMEs.
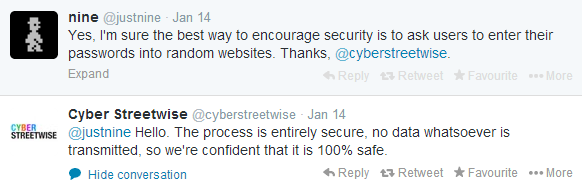
Unfortunately, what started as almost childlike enthusiasm quickly turned to anger & utter frustration after reading the following tweet...
Excuse me for a second. I'll be right with you...
*** In this industry, nothing is "entirely secure" or "100% safe" ***
Here's what they're referring to...
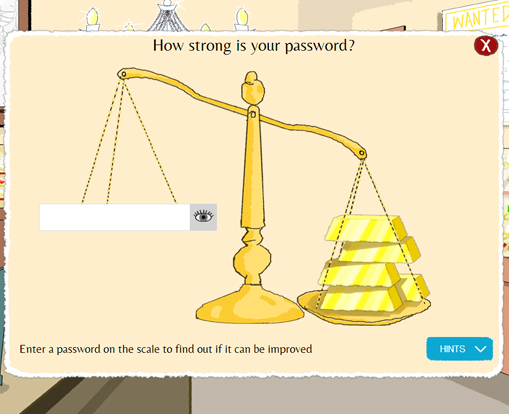
Passwords
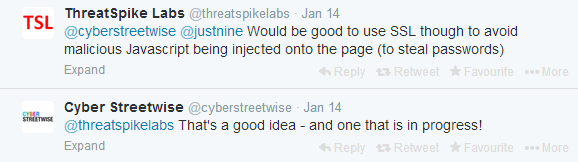
It's worth noting that during this exchange with @justnine, cyberstreetwise didn't use any form of SSL encryption, a point raised by another visitor.
It's not "a good idea" - it's absolutely crucial. As "ThreatSpike Labs" mentioned, it's possible for a hacker to inject malicious javascript to collect the user's password. However, even ThreatSpike Labs appear to be missing the fundamental point.
Password strength testing by a 3rd-party is never secure, regardless of SSL. If you enter a password intended for use on one website into another, it becomes weak... regardless of length, contents or cryptographic strength. Someone at CSW must know this; if you dig a little deeper in the library, you're told never to share your passwords with anyone.
Thankfully, that section of the site has now been removed completely.
There's a lot to get through, so let's dive in.
A guide to IT policies and procedures.
"UK regulations protecting customers’ personal data are strictly enforced with fines of up to £500,000, but as importantly your business’ reputation could be damaged if customer data is compromised."
They are, of course, referring to the Information Commissioners Office... another gov't agency with a history of really bad security practices. There's the SSL faux pas from last October and the SQL injection and XSS bugs from 2009 (which are still vulnerable, I might add!)
Thankfully, there's nothing particularly bad in this section. The references to being "closer to complete cyber safety" are a little concerning though!
On to the next building...
Securing your IT.
Keeping your devices safe and up-to-date.
The suggestion here is to keep your operating system, browser and other software up to date... and that's sound advice. However, they go on to say...
"More importantly, older versions are vulnerable to viruses and hackers"
Now that's bad advice for two reasons...
1. The older the software, the more time the vendor has to patch vulnerabilities identified after its general release. You need to apply updates, sure... but upgrading to a more recent version (Windows 7 to Windows 8 for example) doesn't remove the risk of viruses or hackers.
2. New software is just as vulnerable to viruses & hackers... if not more so.
Create a safe wireless network.
CSW recommend the use of WPA2, which is also sound advice... however they refer to it as "password encryption" which either demonstrates they don't understand how it works, or it's not worded correctly. WPA2 doesn't encrypt the password, it encrypts your wireless traffic (only between your device and the router) using your password.
To make matters worse, many routers ship with a feature called WPS or Wireless Protected Setup. Ironically, WPS is totally insecure and should be disabled immediately. It doesn't matter which encryption type you specify (WPA or WPA2), if you use WPS, you're at risk. CSW make no reference to this vulnerable technology!
Banking securely online
Bank safely online
CSW recommend installing Trusteer Rapport - a piece of software designed to reduce the risk of MiTM/MiTB (man in the middle / man in the browser) & phishing attacks. Unfortunately, it's quite easy to bypass. It also sends activity logs back to an Amazon AWS server over an insecure and unauthenticated SSL connection.
Let's skip ahead to...
Shopping online safely.
Make payments safely.
According to CSW, "there is no increased risk in paying by card using mobile websites".
Where do I start?
Most Android & iOS devices still have no support for NPN, OCSP stapling, TLS v1.1/v1.2, elliptic curve cryptography, GCM suites or appropriate BEAST/CRIME mitigation for CBC ciphers. To claim there's no increased risk is absolutely bonkers!
The Library.
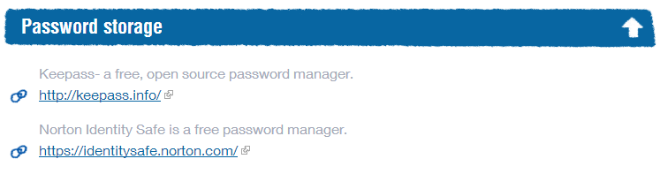
Password storage
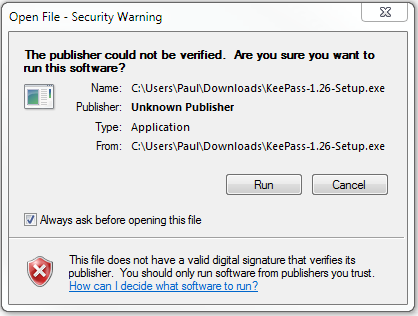
CSW recommend KeePass, a password manager designed to store your crucial passwords safely and securely.
If you're an avid follower and have already read this, you'll probably know what I'm about to say.
KeePass is weak and insecure for a variety of reasons...
1. It's delivered over HTTP, an insecure protocol subject to in-transit modification.
2. The "integrity keys" used to validate the installer are also sent over HTTP, so are easily modified.
3. It doesn't use strong key stretching techniques (PBKDF2 for example). Instead, they opt for 6000 rounds of AES256; which is notably weaker.
But most bizarre of all...
4. It's not digitally signed! The version you're running could have been altered... you'd never know.
If the installer isn't secure and the authenticity of the integrity keys can't be confirmed... you've just undermined the entire process.
Nobody in their right mind would recommend such a program!
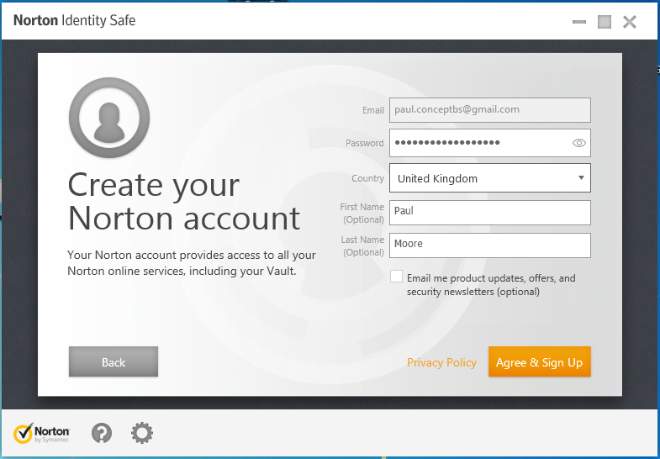
That brings me to Norton's Identity Safe...
Symantec sign their installer, so we at least know it's come from Symantec without being modified in transit. Trouble is, they don't provide any information about their encryption techniques.
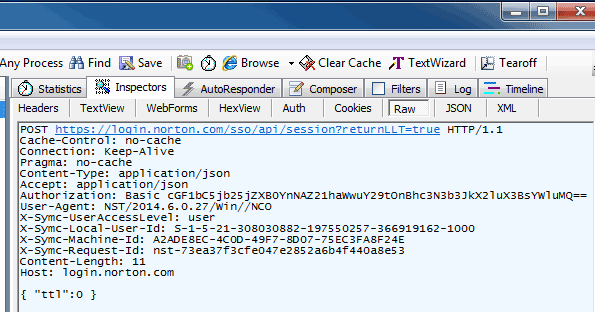
So, let's see if it's safe by registering. I fired up Fiddler and waited for "Identity Safe" to tell me the SSL certificate between myself and Symantec was fake...
The fact we can see the SSL traffic is a sign we're heading down an insecure road... but as you can see, my username/password aren't there, so it's all good, right?
Well, not quite.
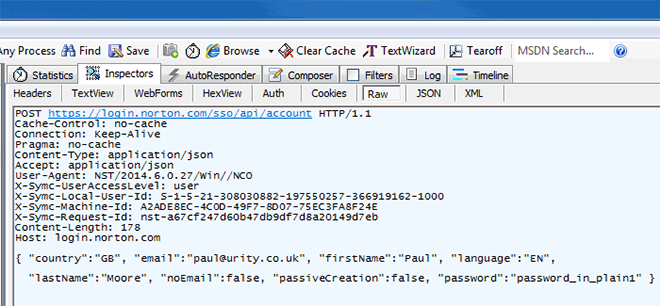
You see, Symantec use HTTP Basic authentication which requires the application to pass a base64 encoded value. As you can see on the "Authorization" line, mine is
cGF1bC5jb25jZXB0YnNAZ21haWwuY29tOnBhc3N3b3JkX2luX3BsYWluMQ==
Run that through www.base64decode.org and guess what...
[email protected]:password_in_plain1
... there's my username & password, clear as day.
It's that time again...
At this point, you're probably thinking...
"Ahhh, but the hacker would need to know how to decode base64 first!"
True, but if base64 is a new concept to our would-be hacker, they don't present much of a risk in the first place. Let's register again with different details and monitor the traffic more closely...
Sigh. So much for "measurably and significantly improving" my online safety.
So far, all these recommendations put the user at much higher risk.
Summary
I'm an advocate for any service which provides useful, accurate security information to consumers and businesses alike. I really wanted to like the cyberstreetwise concept; get behind it and push the idea to our customers.
In reality and unless things change, I'll be doing quite the opposite.