TL;DR - Your master password is sent to Siber Systems and the mobile applications are insecure.
Described by its creators, Siber Systems, as "completely secure using military grade encryption", Roboform has been knocking about since 1999.
Now, I have a rule when testing password managers. If the vendor describes it as "military grade" or "completely secure", I'll set aside 5 minutes to demonstrate why that's never, ever true.
Solid security is a mixture of security & usability; a balancing act made ever-more difficult as the attack surface increases. There are mobile apps, desktop apps, USB data silos, cloud storage and online portals... each one is a potential point of failure. To mitigate this, Roboform uses AES256 encryption; unquestionably strong and used as the basis for nearly all password managers today. Although it facilitates security, it doesn't naturally impart "military grade" security.
Roboform Everywhere Portal:
Any encryption is only as strong as its weakest link. In this case, your master password **should be** all that stands in the way of someone gaining access to your digital life. It's absolutely crucial to pick a long, strong master password and most importantly, keep it private. If you believe the sales blurb, you're led to believe that you and you alone know your password.So, let's login to the online portal and take a look what's going on in the background. (click to enlarge)
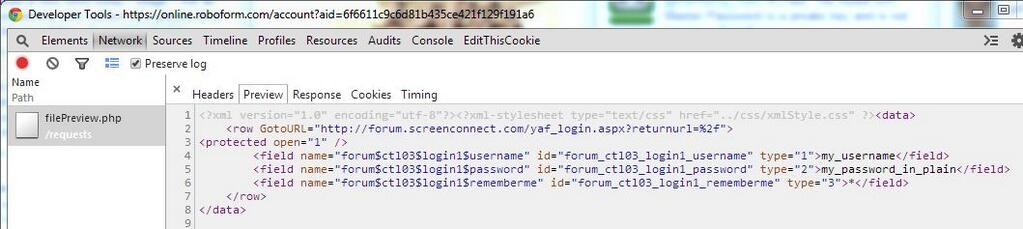
Hang on, those details are being returned in plain text... not encrypted! That means they're either storing them in plain text or they're encrypted and the server knows our master password.
I quizzed Roboform via Twitter.
@Rambling_Rant Paul, we decrypt the data locally, not on the servers.
— RoboForm (@roboform) June 9, 2014
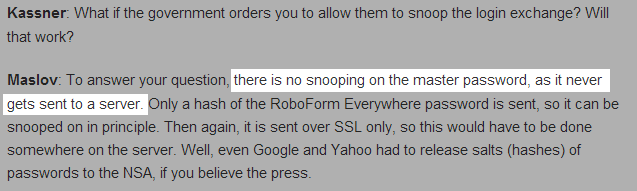
Well that's clearly not the case here, so I dived deeper. A quick Google search revealed an interview with Vadim Maslov, CEO and Founder of Siber Systems, during which he said...
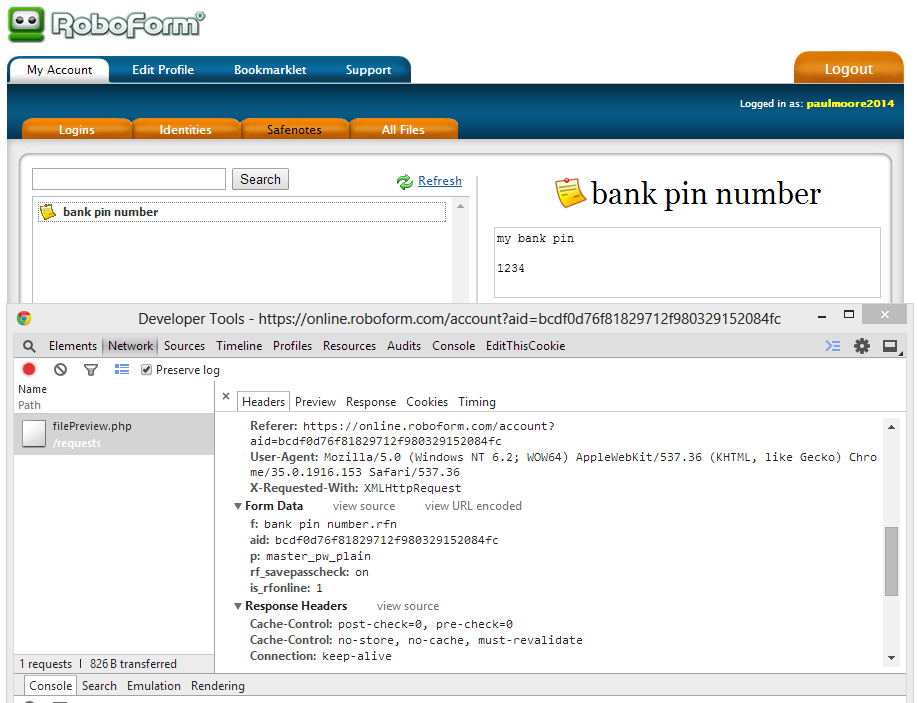
Something doesn't ring true here. They're absolutely adamant that your private master password remains as such, as it's never sent to Siber Systems. I ran the test again, this time watching the network traffic as I entered my master password. (click to enlarge)
Sure enough, there's the master password (see "p" param in form data)... plain as day. No hashing, no KDF... it's sent in exactly the same fashion as any other authentication process. Note "authentication", not encryption.
Now I'm pissed off. If you're going to store my "private" password on the server for the life of the session, at least have the decency to be honest about it. It's a bad design and totally unnecessary.
If you're required to hand over a password, a phrase or indeed anything you know to gain access to your data, that's authentication... not encryption. They may encrypt the data at some point down the line and I see no reason why they'd choose to keep your key, but it doesn't alter the fact the entire process has been undermined from the outset.
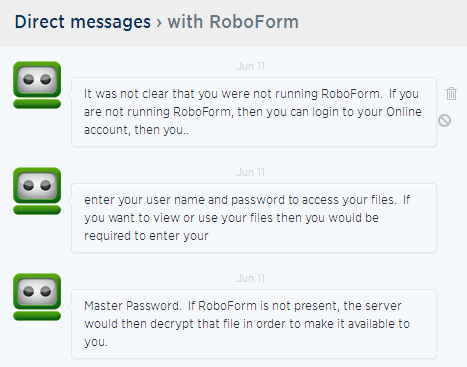
Back to Twitter... this time over DM.
So they do decrypt on the server and they do receive a copy of your master password! What happened to "never sent to the server" Vadim?
It's also worth noting, Roboform was installed throughout these tests. The application was running and the chrome plugin was enabled too.
Roboform Everywhere for Android/iOS
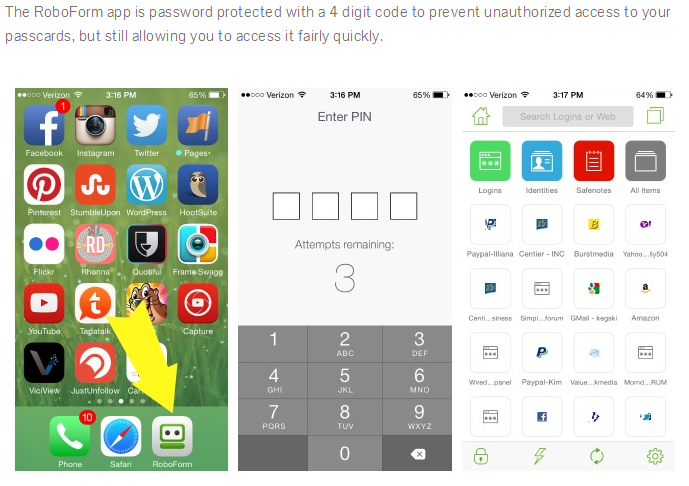
If you haven't yet seen enough to question how safe you are, let's move on to the mobile applications.Like the desktop version, Roboform Everywhere for Android/iOS uses the same AES256-based platform. Unlike the desktop app however, it's laughably insecure. I spotted a review/giveaway offer on Twitter (see http://theysmell.com/roboform) and noticed this screenshot.
So you can access the application with a PIN number instead of the master password, sounds cool... right?
Think about it. Your data is encrypted and only someone with the master password can decrypt it. If you're not entering it, it must be stored on the device along with your data and "protected" with a 4 digit PIN.
Let me make this clear from the outset.
That's possibly one of the most stupid features I've ever seen.
If you're going to replace encryption with authentication, you'd better make damn sure you do it right. Better yet, don't do it at all.On iOS, that 4 digit PIN has just 10,000 possible combinations. A modern PC can count to 10,000 in a heartbeat, but there's a rate limiter which prevents you simply trying every combination. That's easy to bypass though. On Android, there's no rate limiting at all, but you're not limited to just 4 digits either.
So if you lose your phone or it's stolen, you'd be forgiven for thinking this "AES256, military grade, completely secure encryption" would be virtually impossible to break.
Yeah, about that...
So without knowing the master password or PIN, we've gained access to the data. Worse, it's synchronized with the cloud automatically, so any changes would propagate to every other device linked to that account.
Summary
As a cryptographic algorithm, AES256 is immensely strong... and therein lies the problem.Anyone can incorporate AES into their application, but very few do so safely and securely. It's just as important to know how it's built, not just what it's built on. Crypto alone won't save you.
What's the source of entropy?
Which KDF is used, if any?
How are keys handled/transported?
What does the threat landscape look like?
Do you decrypt in segments or in bulk?
How do you obfuscate those crucial keys while in memory?
Are you clearing that memory securely when it's no longer needed?
Where does the encryption/decryption take place?
Do we use any techniques which aren't peer-reviewed or could be classed as "out of the ordinary" or "roll your own"?
... just some of the vital questions which Roboform (and many others) fail to answer.
So next time you hear "completely secure" or "military grade encryption", run a mile. It's a $20 password manager! It's OK...
Two enterprise-worthy password managers: LastPass and RoboForm http://t.co/uP0K2UAfbr by @edbott on @TechProResearch — TechRepublic (@TechRepublic) June 11, 2014
... but enterprise-worthy? I'm not sure.
Don't forget to Like, +1 and RT. Thanks!