Update as of 15/03/13:
I have received a number of emails asking for further comments on the situation @ MyDish.
I firmly believe that every effort is being made to rectify the issues I've identified - and the insinuation that Carol or the team at MyDish have ignored the problem is entirely without merit. Beyond that, I'm not prepared to discuss the matter any further at this stage. If there are any updates, I will update this post accordingly.
MyDish.co.uk is the brainchild of Carol Savage; a successful entrepreneur featured on Dragon's Den back in 2009.
Her pitch convinced Deborah Meaden to invest £100,000 for a 15% share of MyDish. If you haven't seen it, watch it here: http://www.youtube.com/watch?v=GBYBqhEiGbo
It's a great idea - collating thousands of recipes from families across the globe and sending the list of ingredients to your local retailer for delivery. It's a concept which has attracted significant interest; with companies such as BT, Tesco & Coca Cola all exploiting their white-label MyDish platform.
Apéritif
So yesterday (a little belated I know), I decided to join... and oh dear!I can't honestly remember the last time I visited a site which was so unutterably bad, it made my toes curl. According to Carol's pitch, the site/platform had (at that time) cost a whopping £600,000 to develop... and based on 30 minutes browsing the site, not nearly enough went on security.
Ignoring the community aspect for a moment - the purpose of MyDish is to share recipes and send the appropriate ingredients to a supermarket retailer. There's currently support for Tesco, but ASDA might be on the way too.
You'll need 4 key ingredients. Your username & password for MyDish... and your username & password for Tesco.
Main
It's quite a big "main" I'm afraid... so leave room for dessert.Passwords
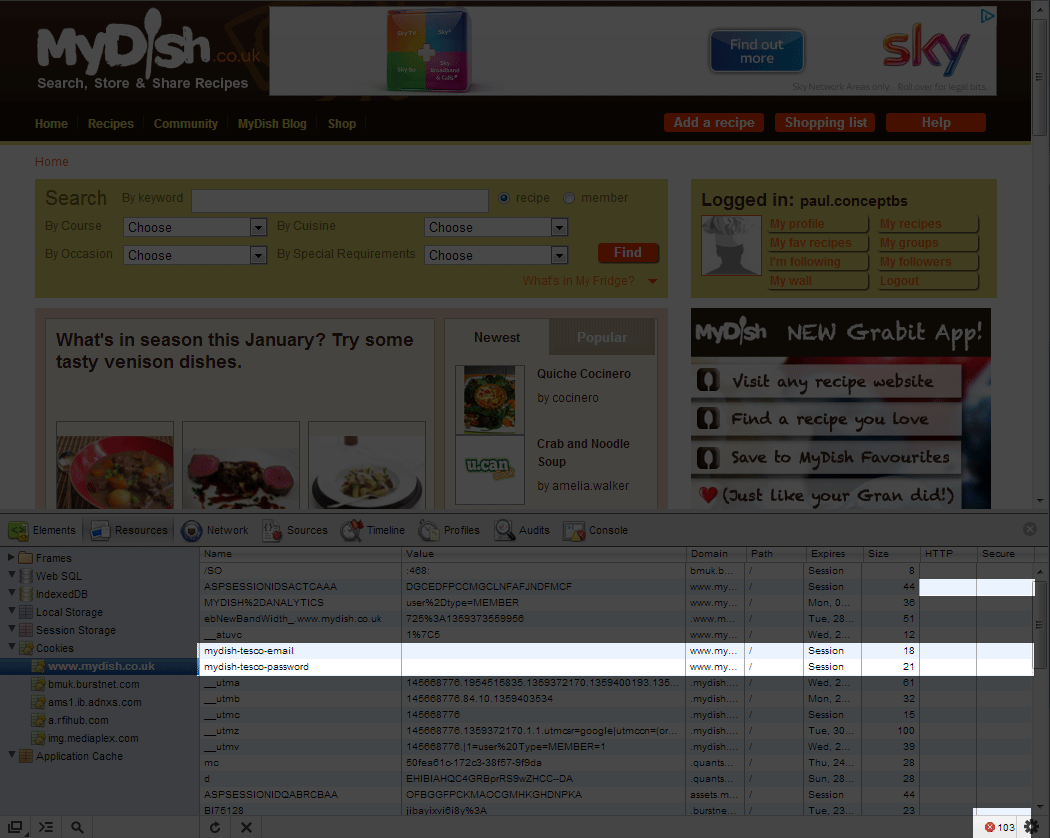
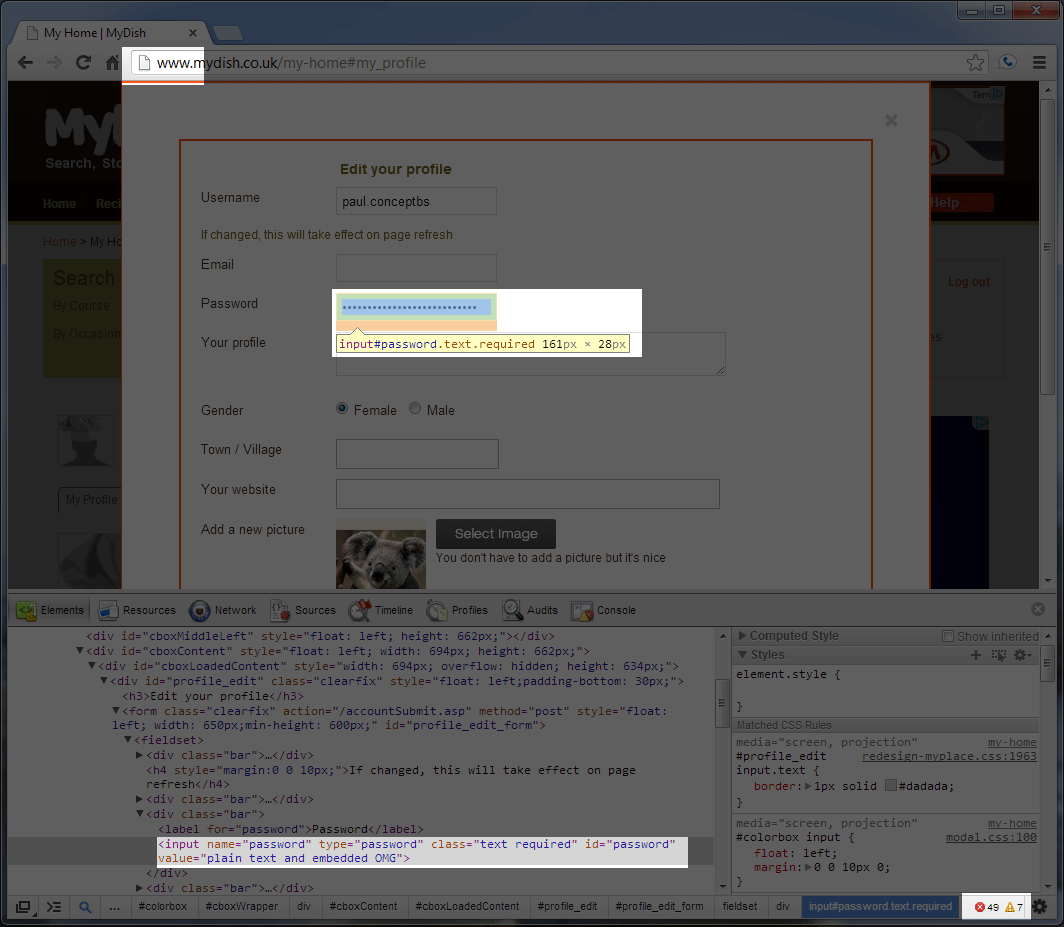
1. Storing passwords in plain text is just asking for trouble. One lost backup, one database breach and you can kiss goodbye to account security... along with user trust & confidence in your business. 2. NEVER, EVER store usernames/passwords in cookies. At some point, it will come back to bite you... or the user.- Never embed passwords in a page - doing so demonstrates you have 1) the user's password, 2) little regard for user safety and 3) a questionable programming style.
Make sure you securely hash passwords - PBKDF2->HMAC-SHA256 or bcrypt with added salt for seasoning. If a user forgets their password, always reset - don't remind!
SSL
Use it. Seriously... there's no excuse. Broadcasting usernames/passwords without encryption is akin to walking down the street screaming your personal information. They cost from just £9.99 a year if you don't require extended validation or insurance.Cookies
The ingredients you will need are:- SSL (see above)
- The secure flag.
- The httponly flag.
MyDish doesn't use SSL, so cannot use the "secure" flag... and chooses not to use httponly. Not a great start! Remember - you're trusting them to keep your Tesco login information safe.
Access Control List / Authentication
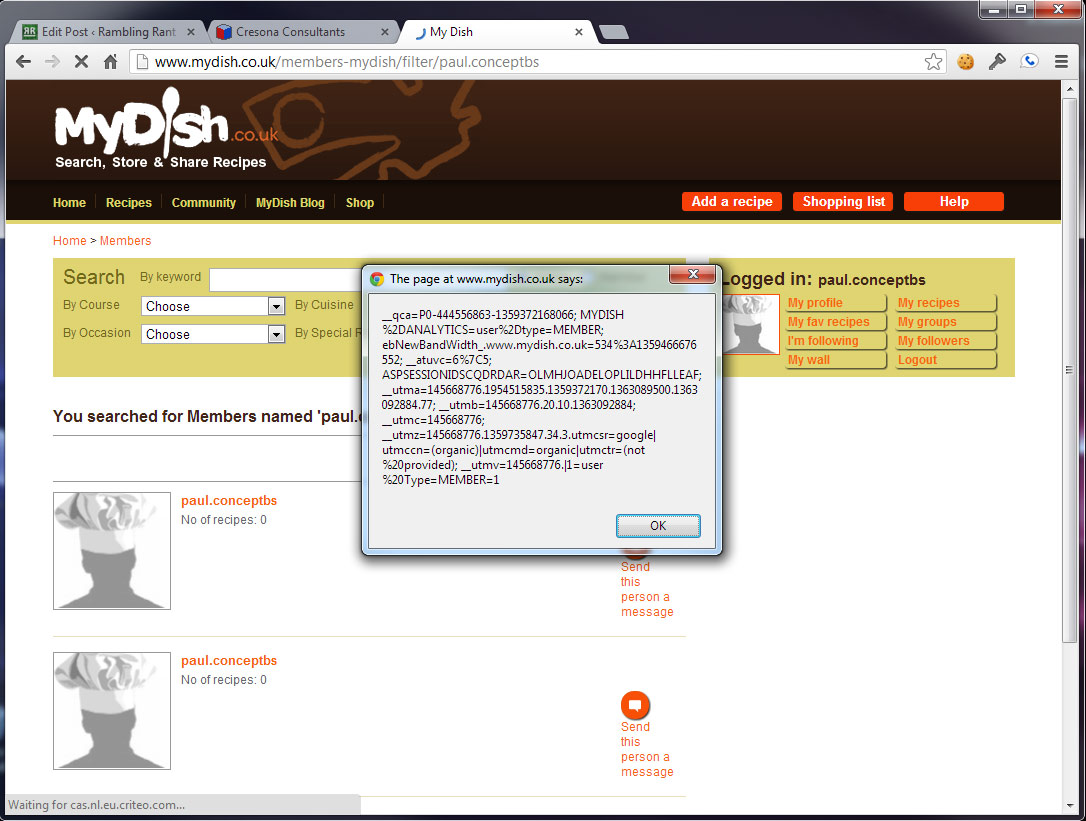
Not to put too finer point on it... it's broken. Completely and utterly broken.Multiple users can share usernames, email addresses and worse, you can change other user's passwords too. You can even login without a username or password! Clever.
Cross Site Scripting
The entire site is vulnerable to both stored & reflected XSS - making the simple process of reading a recipe a potentially hazardous task. If you're logged in and view my recipe, I'm now logged in as YOU. I have your session information, including your MyDish username, email address AND your Tesco username & password. With the urge to place a massive order on your card successfully curbed, let's move on.SQL Injection
The database contains everything - recipes, schema (design), user information... the lot. Securing it properly is the difference between success & failure. If a rival gets hold of your design, it can be cloned & improved... not to mention the risk it poses to your users. Unfortunately, there are a number of SQL injection exploits... all visible because of overly-verbose errors and method exposure."sp_mydish_recipe_getRecipe" for example, tells you exactly which column failed and the data it expected... all useful info for any would-be hacker.
Dessert
Security aside, even the basics don't work. Take the help button for example... it tries to load mydish.co.uk/news/841 but throws a 301 (Moved) and takes you right back to the homepage.You'd better hope you've logged in using Facebook, or you're bombarded with errors because the Facebook API can't find your details.
Summary
If your company handles user information (or facilitates access to sites which contain personal information) - please, hire an expert to design your application/site.The site has more holes than Swiss cheese. If you want/need to use the service, do so mindful of the fact your details, including your Tesco username & password, are visible to everyone. My advice - stay well away... at least until they hire a competent team of developers.
Disclosure Notes:
29/01/2013: First email to Carol. No detailed information provided, just asking who to send the information to.
30/01/2013: Followed up with a call to Carol's mobile. We discussed the situation. I later forwarded a detailed list of every issue which needed to be addressed - with a request to email me to confirm receipt.
31/01/2013: No response, so another email to confirm receipt of the last email.
06/02/2013: Still no response. Another email sent, followed up with another call. Email had arrived, just hadn't replied.
12/03/2013: Still no response. Courtesy email sent to advise of the intention to publish this post.